- Resilient Cyber
- Posts
- Resilient Cyber Newsletter #16
Resilient Cyber Newsletter #16
Cyber Standards for the American Healthcare System, AI SOC Analysts, CA Veto's AI Bill, Cloud Indicators of Compromise (IoC), and the Complete Guide to Non-Human Identities (NHI)'s
Welcome!
Welcome to another issue of the Resilient Cyber Newsletter.

If things look/feel a bit different, it is because I’ve been working to migrate from Subtack to BeeHiiv. While I enjoyed writing on the Substack outlet, I’ve heard nothing but amazing things from friends such as Clint Gibler of tl;dr sec and Mike Privette of Return on Security.
I’ll be exploring the BeeHiiv platform while still bringing you weekly newsletters with resources and deep dive write ups, analysis, interviews and more - so stay tuned and enjoy!
Cybersecurity Leadership & Market Dynamics
The American healthcare system has been victim of several highly visible and impactful cybersecurity attacks. From ransomware to events such as UnitedHealth, these incidents continue to fill the headlines, with incidents impacting care, payments and patient privacy.
That is why it should come as no surprise that Senators are looking to introduce legislation to improve cyber in the American healthcare system. Senators Wyden and Warrner introduced what is being called the “Health Infrastructure Security and Accountability Act” which will require HHS to develop and enforce tough minimum cyber standards for healthcare providers, health plans and clearinghouses.
While the details are still being developed, it includes potential jail time for CEO’s who lie about their organizations cyber posture and also lifting the cap on financial punishments under HIPAA, as well as funding for rural and urban hospitals who lack resources.
We’ve seen cybersecurity insurance price hikes start to stabilize. Over the last several years, incidents such as Ransomware led to insurance price hikes, along with insurers holding organizations accountable for having security fundamentals in place and doing more due diligence around ensuring organizations have foundational practices for security.
This article cites research from Fitch Ratings showing insurance premiums rose 50% in 2022 alone. It states organizations seeking cyber insurance have improved cybersecurity hygiene. This demonstrates that the need for insurance and stricter standards from insurers is forcing organizations to take their security hygiene more seriously.
Insurers are also now looking for organizations to actually prove a baseline of security, due to stricter underwriting processes for policies. I personally think cyber insurance requirements and increased cyber regulation will do more to bolster security than any voluntary efforts such as CISA’s Secure-by-Design pledge or other voluntary, self-attested type activities. Ultimately, organizations will only do as much security as they are forced to do by either market or regulatory forces.
A image shared by Coatue helps visualize just how few U.S. technology IPO’s occurred during 2022-2024, which is less than both the post dot-com bubble (2001-2002) and the financial crisis (2008-2009).

Thought provoking article from CSO Online showing that surges in security spending are focused on software and services, rather than staff. The article discusses how most security budget growth is going towards products, infrastructure, tooling and external services, such as consulting, managed services and professional services, versus internal staffing and team growth.
The paradigm shift leads to CISO’s and teams needing to focus on strategic planning and integration over day-to-day security activities, as more of their tooling, and operations is fueled by external products, services and consultancies.
Several studies are cited, showing cyber workforce growth is stagnating, partly due to lack of budgets to grow internal security teams leading to hiring slowdowns and outright freezes in some cases as well. The change is forcing CISO’s to focus on keeping boards abreast on cyber risk, and orchestrating relationships and engagements with external software and services suppliers as well, which has its own risks with issues such as supply chain security.
AI
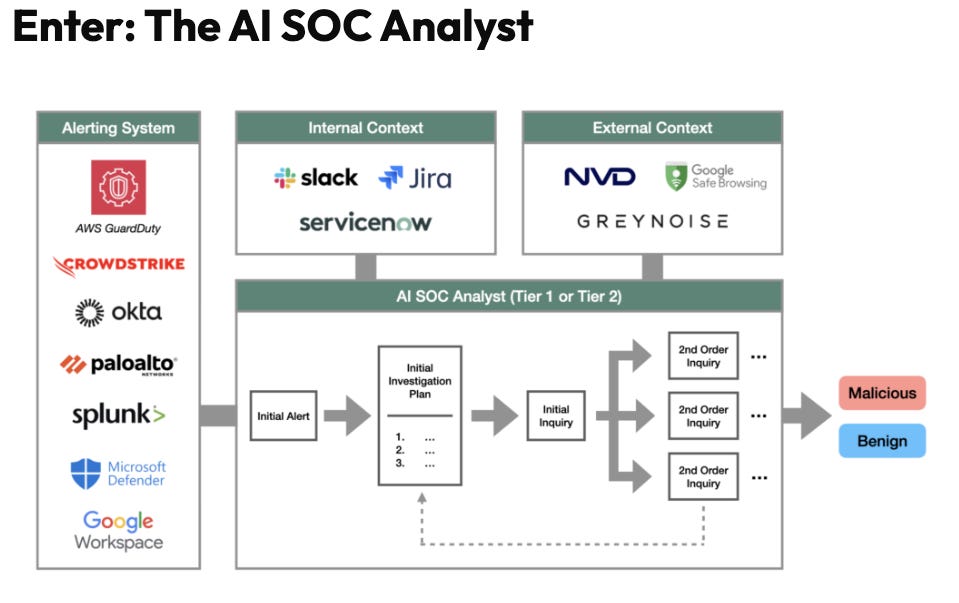
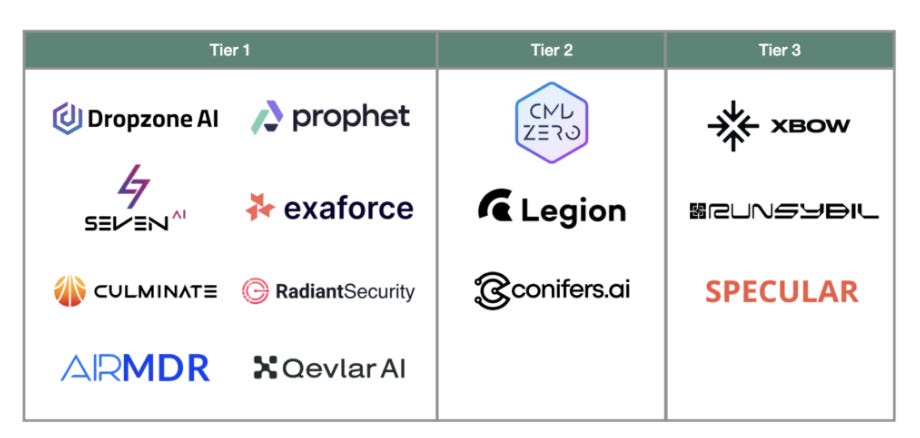
There is a lot of excitement about the potential for AI to aid security. One of the most promising areas is that of the SOC, which often includes massive amounts of data, cumbersome manual activities and escalations and terrible struggles with burnout and fatigue for those operating in the role.
This article from Scale Venture Partners discusses the potential for AI SOC Analysts as well as some companies currently focusing on the challenge.
Many have taken to social media recently to point out that they feel the EU is being left behind when it comes to AI and related innovations. While the U.S. is taking a light touch, often voluntary and guideline based approach to AI security and governance, the EU instead has taken a bit of a more rigid approach focused on compliance, restrictions and fines.
In true meme fashion, folks have pointed out how the leading AI unicorns are all coming out of the U.S. versus the EU, as well as the fact that the latest features such as Apple Intelligence won’t be available to EU consumers.

The perspectives on the topic vary, with those in the startup, tech and venture communities being very frustrated with the situation, feeling like the EU will continue to be left behind, struggle to really compete in the technology and startup landscape, while others on the side of ethics, or compliance and so on feel like it is a valid tradeoff and approach.
Considering how critical AI and software is for everything from consumer goods to critical infrastructure and national security, I sympathize with the concerns of being left behind, and know compliance while needed can also often have unintended consequences and impacts.
We continue to see organizations and the broader security industry try and keep up with the adoption of AI, GenAI and LLM’s when it comes to security and governance.
This is a good article from Stealth Net AI discussing popular frameworks such as NIST AI RMF, ISO 23894, and the EU AI Act. It also discusses the need for security tooling and teams, such as AI firewalls, vulnerability scanners and red teaming to secure AI systems and go beyond compliance and frameworks and get more technical and tactical as well.
California Governor Newsom recently vetoed SB-1047 or “The Safe and Secure Innovation for Frontier AI Models Act”, which had previously passed the state’s legislature on August 28th 2024.
Many considered it to be the world’s most “stringent” set of regulations when it comes to governing AI. This article from CSO Online summarizes the story, including the fact that CA had previously passed other AI regulation and bills. The stated reasons include concerns it was falling short of providing a flexible, comprehensive solution to curbing the potential catastrophic risks of AI, and fears it would stifle innovation. Newsom pointed out that the bill targeted the largest models but neglected concerns with smaller models, which could be equally as risky.
California is home to 32 of the world’s 50 leading AI companies. This decline to pass the bill represents CA’s commitment to ensuring they stay in the leading role and also Newsom points out that any framework to effectively regulate AI needs to keep pace with the technology itself, which of course is difficult for regulation to do given how quickly the AI space is evolving.
This represents the stark difference in approaches between the U.S. and EU, with the former having a concern with stifling innovation rather than putting fears around safety and security above all, even to the detriment to consumers and economic prosperity.
Wiz has also published an AI Security 101 Guide that I found useful. It covers:
AI Risks and best practices for mitigation of critical risks
How to safeguard your AI development pipeline with AI-SPM
Using AI to power security, including operations and incident response
As AI security continues to heat up, it is key for us to make use of resources to ensure organizations we’re collaborating with are moving out smartly.

AppSec, Vulnerability Management and Software Supply Chain Security
Wiz published a comprehensive article diving into IoC’s that are specific to the cloud. For those unfamiliar, IoC’s are a core part of security programs are commonly mean criteria such as artifacts and evidence that can indicate either an ongoing or past security breach. These are artifacts and remnants of malicious actors and their activities in an environment.
The blog points out that traditional IoC’s don’t account for nuances of the cloud, such as IAM metadata and control plane API calls, which often can provide insight into nefarious data gather or targeting of credentials for abuse. The blog covers both behavioral and atomic IoC’s, with the former being based on threat intelligence and active malicious activity which is dynamic and changes, while the latter is more static and well-known.
Wiz also published a GitHub repository of atomic IoC’s for the community to leverage.
Utilizing IoC’s is critical for activities like threat hunting to identify ongoing or past incidents that impacted the organization and this blog provides a masterclass on dealing with Cloud IoC’s, great work as always by the Wiz team for providing this to the community!
I’ve talked a lot recently about the challenges that exist in the NIST National Vulnerability Database (NVD) backlog. There are currently THOUSANDS of CVE’s in the NVD that lack enrichment with details such as CVSS, CPE and CWE, which are used to prioritize vulnerabilities, understand what products they impact, as well as their root causes.
Vulnerability Researcher Patrick Garrity of VulnCheck recently did a deep dive into the vulnerability backlog and found some really alarming findings, including:
As of September 21, 2024, 72.4% of CVEs (18,358 CVEs) in the NVD have yet to be analyzed (compared to 93.4% as of May 19, 2024).
As of September 21st, 46.7% of Known Exploited Vulnerabilities (KEVs) remain unanalyzed by the NVD (compared to 50.8% as of May 19, 2024). Of the 197 KEVs, 92 have yet to be assessed by the NVD (Source: VulnCheck KEV). A* s of September 21, 2024, 85.9% of CVEs added to the NVD since February 12 now have a CVSS record, leaving only 14.1% without a CVSS score.
VulnCheck believes that NVD’s embrace of CISA’s Vulnrichment as a data provider for CVSS enrichment has been a notable success.
You can see some of the insights in the visualizations below as well:


We continue to hear phrases such as “identity is the new perimeter” when discussing cybersecurity, and trends such as the push towards Zero Trust. We also know from reports such as the Verizon DBIR that compromised credentials remain among the most prominent sources of incidents and attacks.
If identity is indeed the new perimeter, that perimeter is porous, as we look at the current identity landscape. This recent piece from Francis Odum of the Software Analyst lays out just how problematic the landscape is, with his article “The Complete Guide to the Growing Impact of Non-Human Identities in Cybersecurity”.
I have covered NHI’s in several recent articles, such as:
Francis’ piece is a comprehensive breakdown of the rising ecosystem for NHI’s. It discusses currently fragmented processes and approaches to managing NHI’s today, the current vendors and tooling in place and their gaps and a proposed future identity stack. If you are interested in identity security, I strongly recommend giving this one a read!


There’s been a ton of discussion around Software Bills of Materials (SBOM)’s. From the Cyber EO, OMB Memos, CISA and others. I have even written extensively about the topic in my book “Software Transparency” from Wiley.
While the SBOM requirements were dropped from CISA’s Self-Attestation form, it appears other arms of the Government are moving full speed ahead. One of those is the U.S. Army, who released a “SBOM Policy” memo, aimed at implementing the Army’s policy for the use of SBOM’s to “enhance software supply chain risk management practices and effectively mitigate software supply chain risks”.
It builds on the Cyber EO, along with OMB memos 22-18 and 23-16 and the Army’s own Directive 2023-16 “Supply Chain Risk Management for Weapons Systems” and the Arm’s Directive 2024-02 “Enabling Modern Software Development and Acquisition Practices”, the latter of which emphasized the Army’s reliance on software and needing to understand and mitigate risks to that software and its systems.
The requirement has a very broad scope, covering software developed exclusively with Government funds, including Government-off-the-shelf Software (GOTS) and developed by Contractors using contract funds, and any commercial software, as well as open source software.
Interestingly, it does not include cloud services, but I suspect that is because as an industry, we still struggling with defining SBOM’s for cloud, especially SaaS, often called “SaaSBOM’s” as coined by Walter Haydock and I in an article dating back to 2021 titled “The Case for a SaaS Bill of Materials”. CISA does have a working group still flushing this out and has published guidance around SBOM’s for cloud.